Single Sign In (SSO) with SAML
Description
Access Freedcamp with corporate credentials using SAML based SSO - leading industry standard for exchanging the authentication and authorization data. Freedcamp supports Microsoft Azure AD, Google, Okta and AWS SSO.
Enterprise plan users can access Freedcamp with corporate credentials if SAML-based SSO (SSO/SAML integration). Single sign-on (SSO) is the general term for the various techniques which allow users to access multiple applications from a single authorization point, which is managed by an identity provider (IDP). Freedcamp, as a service provider (SP), supports Security Assertion Markup Language (SAML 2.0) - a leading industry standard for exchanging the authentication and authorization data. No actual passwords are transferred during the Freedcamp authorization event. Instead, Freedcamp receives a SAML assertion of the user identity, which is valid for a limited period of time and digitally signed.
Mobile
SAML/SSO is fully supported for authorization on mobile applications including Private Cloud customers (Enterprise customers running Freedcamp in the isolated single-tenant environment).
Provisioning
Freedcamp SSO implementation does not provide automatic users provisioning and de-provisioning. Once a user is invited to one or more of your projects - a user can use SSO to sign up and sign in. For de-provisioning, you can remove a user from your account in Freedcamp and restrict Freedcamp authorization in your company SSO environment. Any of these actions will by itself remove user's access to your projects in Freedcamp.
Dependency
As mentioned above SSO requires a Freedcamp user to have Enterprise plan subscription. Also to enable SSO/SAML White Label should be enabled first.
You can see an example of Freedcamp authorization pages with a white label and SSO with Azure enabled. Email and password sign-ins and sign-ups are only allowed for an account owner (to prevent self-locking) as well as 3rd party users you may want to invite to your projects (customers, partners etc.).
Microsoft Azure Active Directory (AD)
Freedcamp is added as a gallery AD application which allows companies not having premium Azure AD subscription to use Freedcamp SSO.
Please learn more in Freedcamp documentation.
Okta SSO
Freedcamp SSO/SAML supports Okta as IDP but not listed as Okta application. Manual setup is pretty obvious - please contact your account manager for instructions.
Google SSO
Freedcamp SSO/SAML supports Google as IDP but not listed as Google application. Manual setup is pretty obvious - please contact your account manager for instructions.
Settings
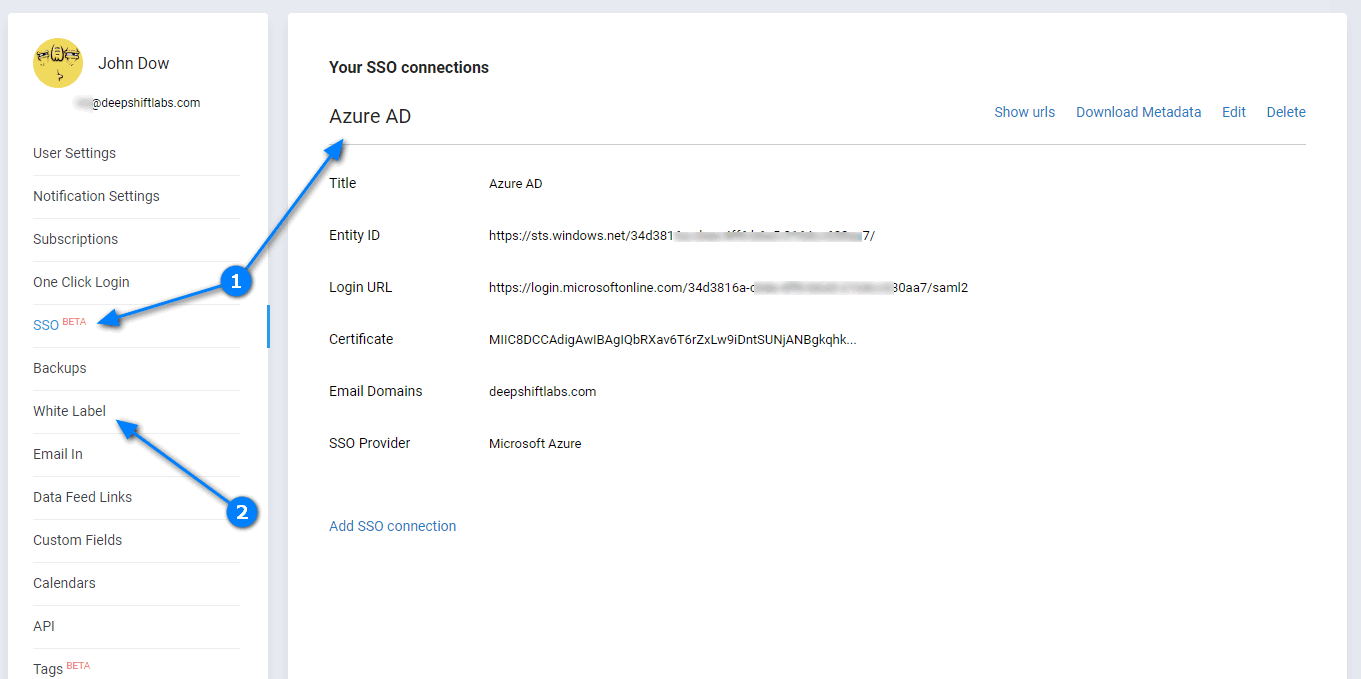
(1) SSO settings are available under My Account. You can set multiple IDPs if necessary. For example, authenticate @company.com users via Azure AD and @company.au via Okta if your company divisions are using different SSO IDPs for users participating in Freedcamp projects.
(2) enable White label on own or *.freedcamp.com subdomain first
The account owner is the only person, with SSO enabled email domains, who can sign in with either Freedcamp user name and password (email) or via SSO. Users in set email domain invited into SSO enabled account can only use SSO to sign up and sign in.
All users invited into your Freedcamp (customers, partners) having emails different from those with enabled SSO can sign in and sign up as usual via email and password and still be part of your projects.